Description:
Belarus – Electronicon – PPC – 250 pts
EN: This task is one of the methods for the psychological attacks. It is intended for people who don’t have heart diseases and reached 18 years 😉h4ck1t{flag.upper()}
As the attached file says, it was real pain. I opened the file in the browser and saw this horrible thing:

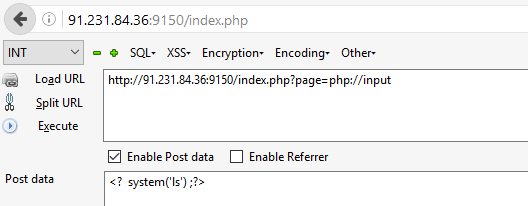
Looks bad and it crashed my browser. This text file was too big for it to handle. So I opened it on Notepad++ and it was’t any better:
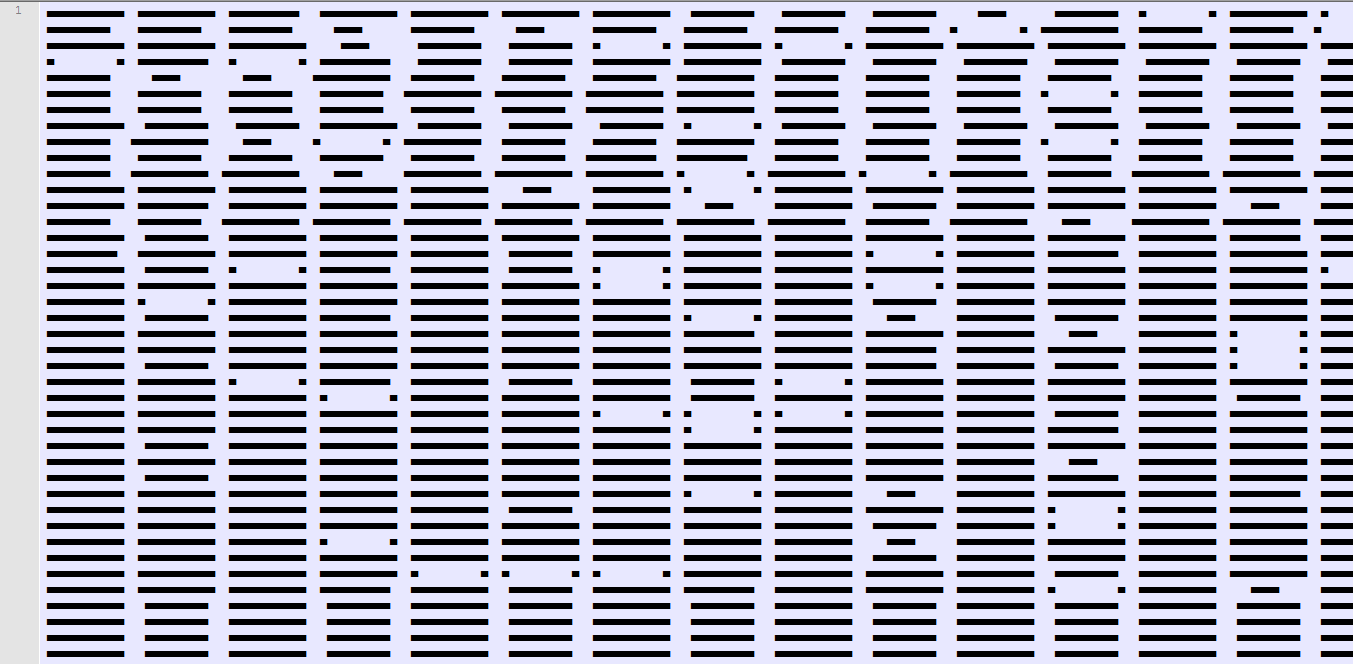
Still terrifying and it was heavy for notepad++ also. But this time something catched my eye. Look at the rows panel on the left, it says only 1 line. Let’s cancel word wrap (View > Word wrap) and check what it is:
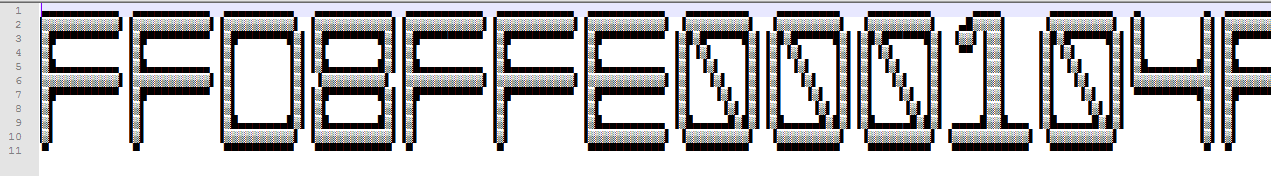
Aah ah! It was a HUGE ascii-art. How huge? 11 rows of 1830661 chars each! It’s a long hex string. So now we need to parse it. I tried using this module but without any success so I decided to go for the hard way. I parsed it myself.
First, I edited the file in order to make it easy for me to parse it. I wanted that every char will be in it’s own line. I wrote a script to separate the characters:
import os
fin = open('pain.txt','r')
fout = open('out.txt', 'w')
content=fin.read()
splitted=content.split('\n')
width=13
print len(content)
for j in xrange(len(splitted[0])/width):
for i in xrange(len(splitted)):
fout.write(splitted[i][:width]+"\n")
splitted[i]=splitted[i][width:]
Now let’s open the edited file with EmEditor that is capable of open large files and see how our file is looking like:
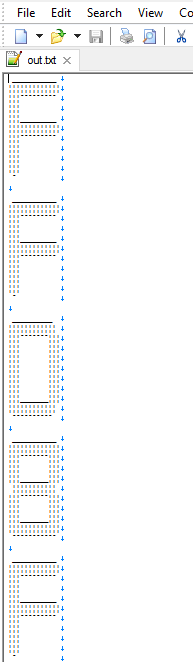
Good! Looks exactly like I wanted! Now in order to parse it we need to tell the code how every letter or digit is looking like so I started to define variable for each letter or digit with the matching ascii-art. It was something like that:
f_in = open('out.txt', 'r')
ff = open('flag.txt', 'w')
content = f_in.read()
content = content.split("\n")
f = content[0:11] # The letter f
c8 = content[37:48] # The digit 8
... # Another letters and digits
... # Another letters and digits
... # Another letters and digits
index = 0
while True:
lines=content[index*12:(index+1)*12-1]
if lines==a:
ff.write("a")
elif lines==b:
ff.write("b")
elif lines==c:
ff.write("c")
elif lines==c0:
ff.write("0")
elif lines==c1:
ff.write("1")
elif lines==c2:
ff.write("2")
elif lines==c3:
ff.write("3")
elif lines==c4:
ff.write("4")
elif lines==c5:
ff.write("5")
elif lines==c6:
ff.write("6")
elif lines==c7:
ff.write("7")
elif lines==c8:
ff.write("8")
elif lines==c9:
ff.write("9")
elif lines==d:
ff.write("d")
elif lines==e:
ff.write("e")
elif lines==f:
ff.write("f")
index+=1
I took the long hex-string and paste in hex editor. It was this photo:
Well, that’s it. We got the flag and we now can rest in peace.
Flag: h4ck1t{1_L0V3_3P1C_F0NT$}