Description:
Find the clam and open it to find the pearl.
out.img
We are given with a file. I ran file command on it to figure it’s file type:
[Megabeets] /tmp/CSAW/clam# file out.img out.img: x86 boot sector
Ok, we have raw image file which will probably contain file/s with the flag. I’ll show 2 methods, choose your preferred one.
Method 1: Autopsy
Open Autopsy (my favorite forensics software, it’s free and heartily recommended) and choose the “Create New Case” on the Welcome window. You can also create a new case from the “File” menu.
Fill the requested details and press “Finish”. Now add input data source to the case. Click “Case” > “Add Data Source…” or on the “Add Data Source” button ( ![]() ) on the main window and choose our file,
) on the main window and choose our file, out.img.
I cannot teach you about all the features of this great software so I’ll just show the path to the flag. If you’re not familiar with Autopsy I recommend you again to start working with it.
In the right panel you can find plenty of features, I will use only the directory viewer. Clicking on the data source (out.img) will show the files in the main directory of the image.
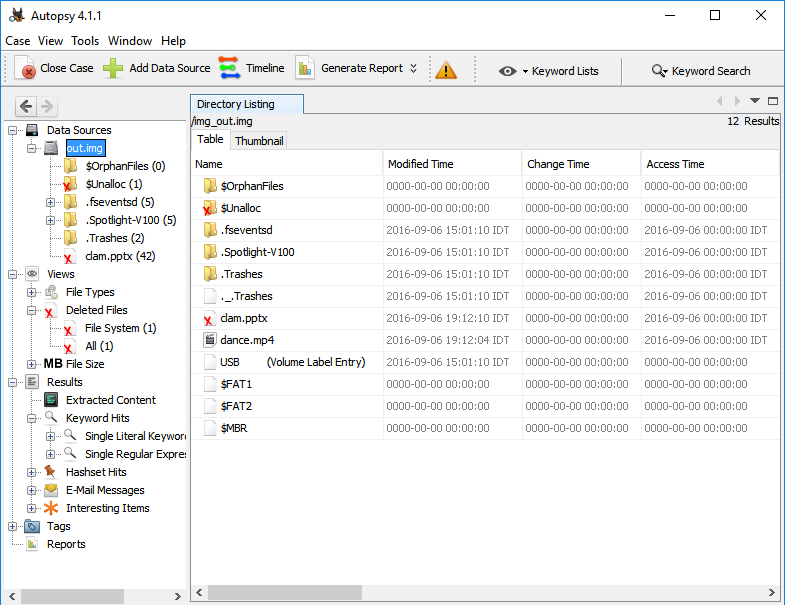
Do you see it? As it says in the description, we found the clam(.pptx)! The X on it’s icon means that this file was deleted from the operation system (but not from the disk). Double clicking it and you’ll see bunch of image files, one of them, called image0.gif, is looking like a MaxiCode. Is it?

Scan it either online or offline to reveal the flag. I was scanning it with this site.
flag{TH1NK ABOUT 1T B1LL. 1F U D13D, WOULD ANY1 CARE??}
Method 2: Foremost
This is less elegant way to solve the challenge. Run foremost on the file:
[Megabeets]$ foremost out.img
You’ll get a folder named output with zip file, movie file and pptx file. Extract the pptx file using 7-zip (PPTX is an archive file), go to the /ppt/media folder and you’ll find the MaxiCode image mentioned before.
