Description:
[!@# a-z $%^ A-Z &* 0-9] [1,3]
All we got is a file and regular expression.
Lets run
file command on the file to determine its type:$ file ./file.kdb file: Keepass password database 1.x KDB, 3 groups, 4 entries, 50000 key transformation rounds
The file is KDB file which is Keepass password database. Keepass is a famous opensource password manager.
I tried open it using KeePassX for windows, but we need a password to open the database. The password probably should match the regex, so I generated a dictionary with all the possible passwords (more then 300,000 words).
import string
import itertools
# strings match the regex
chars = string.lowercase + string.uppercase + string.digits + '!@#$%^&*'
f = open('dict.txt','a')
all_permutations = list(itertools.permutations(chars,1))+ list(itertools.permutations(chars,2))+ list(itertools.permutations(chars,3))
for p in all_permutations:
f.write(''.join(p)+'\n')
And I the ran John the Ripper to crack the password and went to eat lunch.
$ keepass2john file.kdb > kp $ john --wordlist=dict.txt -format:keepass kp Using default input encoding: UTF-8 Loaded 1 password hash (KeePass [SHA256 AES 32/64 OpenSSL]) Press 'q' or Ctrl-C to abort, almost any other key for status k18 (file.kdb)
When I came back I saw that John found the password, now lets open the file:
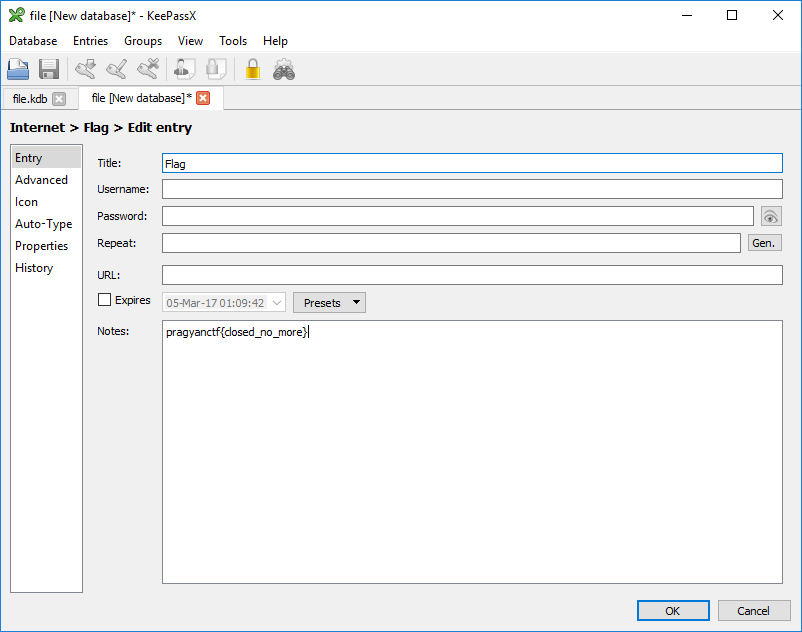
The flag was pragyanctf{closed_no_more}
